Posted on:
June 12, 2014

Posted on:
June 12, 2014
Jun 08 2014
This is the release of a new version of Kippo-Graph, incorporating various fixes.
I decided to mark this as the first major release of Kippo-Graph as it seems mostly “complete”.
Download: kippo-graph-1.0 or clone/pull from GitHub: https://github.com/ikoniaris/kippo-graph
MD5 Checksum: CDFD4D9ACC1B80475A5A2D009C79D262
SHA-1 Checksum: 5B7FE645223BFBD43BE66C51A3DC592B5178EF47
CHANGES:
Version 1.0:
+ Various fixes and updates.
For comments, suggestions, fixes, please use the Kippo-Graph page: /kippo-graph
Posted on:
June 5, 2014
Posted on:
June 4, 2014
Apr 28 2014
The Kippo2ElasticSearch script has been updated and now creates proper entries with all attributes needed for each SSH login attempt. I have also included an exported Kibana dashboard file that you can import in your own instance and visualize the results. This is going to be very useful and it looks great.
Please get/update by cloning/pulling from GitHub: https://github.com/ikoniaris/kippo2elasticsearch
Attached are two sample screenshots of how the Kibana dashboard looks like. This doesn’t need any configuration. Just transfer your Kippo MySQL database with Kippo2ElasticSearch, open Kibana and import the JSON file from the repo and you will immediately see similar statistics for your data.
For comments, suggestions, fixes, please use the Kippo2ElasticSearch page: /kippo2elasticsearch
Mar 31 2014
Continuing from my previous post, here is how to create an attack heat map in seconds using the same ElasticSearch + Kibana instance. First of all we have to download Maxmind’s GeoIP database. The general procedure is super easy (no need to do it):
wget -N http://geolite.maxmind.com/download/geoip/database/GeoLiteCountry/GeoIP.dat.gz gunzip GeoIP.dat.gz
This will output a single GeoIP.dat file which is a binary format with IP to geolocation data mappings which you can query using an API. The Python version of the latter is easily installable via pip (do this):
pip install GeoIP
Bear in mind that you’ll probably get the “clang: error: unknown argument” failure message but fear not; I have written the solution here if you need it: /bypassing-clang-error-unknown-argument.html
We then have to modify the script I posted a little bit, in order to save the two letter country code in the JSON documents before indexing them in ElasticSearch. I have actually decided to pursue this project and publish the (poorly written at this stage, serving as an example) code properly. So just get the Kippo2ElasticSearch files from GitHub:
git clone https://github.com/ikoniaris/kippo2elasticsearch
It includes the GeoIP database, no need to get it yourself. Edit the MySQL and ES values and you’re ready. After importing the data to ElasticSearch, open Kibana and add a new map panel:
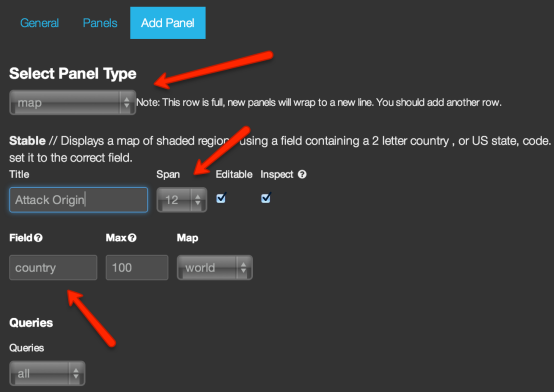 And voilà, scroll down and you’ll have a heatmap of attacks:
And voilà, scroll down and you’ll have a heatmap of attacks:
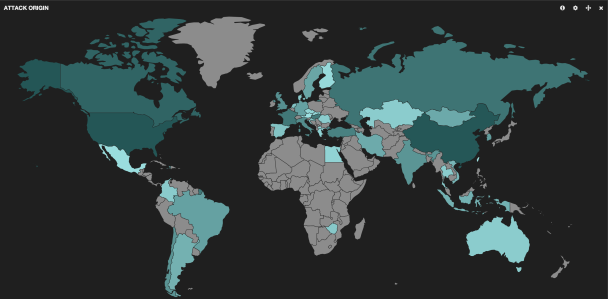 Do you really need more convincing about the prospects of a project combing honeypots with ElasticSearch + Kibana?
Do you really need more convincing about the prospects of a project combing honeypots with ElasticSearch + Kibana? ![]()
For comments, suggestions, fixes, please use the Kippo2ElasticSearch page: /kippo2elasticsearch
Mar 30 2014
I have been investigating ElasticSearch and Kibana for some projects lately and I’ve come to appreciate the easiness of using the two pieces of software together for storing and visualizing data.
This will be an introductory post to something bigger, but I just want to throw the idea out there: let’s transfer honeypot data to ElasticSearch and use Kibana for easy visualization and creation of dashboards.
For Kippo, it all starts with the MySQL database. Our first move is to transfer entries from the DB to ElasticSearch. Now, EleasticSearch accepts JSON documents as input, so we’ll have to convert MySQL rows to JSON objects. The second step is to send those JSON objects to ElasitcSearch for indexing.
The obvious table to convert and send to ElasticSearch is the “auth” table which contains login attempts (timestamp, username, password, success, etc). Here is a quick Python script to do just that (you will need pony and pyes):
#!/usr/bin/env python
import pony.orm
import pony.options
import collections
import json
import pyes
mysql_host = 'localhost'
mysql_port = 3306
mysql_user = 'username'
mysql_pass = 'password'
mysql_db = 'database'
es_host = 'localhost'
es_port = 9200
# We need this, otherwise pony returns an error during the SELECT
pony.options.MAX_FETCH_COUNT = 999999
db = pony.orm.Database('mysql', host=mysql_host, port=mysql_port, user=mysql_user, passwd=mysql_pass, db=mysql_db)
with pony.orm.db_session:
auth_rows = db.select('SELECT * FROM auth')
es = pyes.ES(es_host + ':' + str(es_port))
for auth_row in auth_rows:
auth_dict = collections.OrderedDict()
auth_dict['id'] = auth_row[0]
auth_dict['session'] = auth_row[1]
auth_dict['success'] = auth_row[2]
auth_dict['username'] = auth_row[3]
auth_dict['password'] = auth_row[4]
auth_dict['timestamp'] = auth_row[5].strftime("%Y-%m-%dT%H:%M:%S")
auth_json = json.dumps(auth_dict)
print auth_json
es.index(auth_json, 'kippo', 'auth')
(a repo for this and similar scripts has been added here: kippo2elasticsearch)
You can then go to Kibana, add a new histogram panel and in seconds (literally) have the following visualization of time based attack summaries:
Another idea is to use an IP-to-country library and include another field in the JSON object that you can then use in Kibana to create a heatmap of attacks, etc. There are generally many possibilities and I would like to gather ideas if you have anything in mind.
As I said this is just an introductory post, I will come back to this idea in the future, publish some proper open source scripts to parse the data and perhaps guides on how to visualize the results with Kibana. Let me know what you think.
Powered by WordPress and the Graphene Theme.