Jan 13 2013
GÉANT: Experiences with IDS and Honeypots
Jan 12 2013
Visualizing Dionaea’s results with DionaeaFR
Hello readers and honeypot enthusiasts. As I was writing a couple of articles on basic malware analysis, I noticed today that a new visualization tool was released for Dionaea malware honeypot! In fact I had in mind to develop something along the lines of Kippo-Graph for Dioanea as well, so I am very happy to have stumble upon it (mostly by accident).
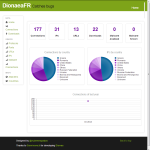
The tool is called DionaeaFR and I’ve found it really helpful in the analysis phase of a honeypot’s activity. It provides a general overview of the malicious connections but it can also zoom in on individual attacks. The fact that’s an aesthetically pleasing utility is also a big plus on my book. The only downside I’ve found is that it couldn’t process a rather large database I had (around 500mb, which btw is normal for Dionaea). The webserver it deploys was being killed after a while, but this could be due to quite low VPS specs.
DionaeaFR is written in Python, uses the Django framework and a number of other libraries, mostly client-side JS. It is maintained by Ruben Espadas. Let me guide you through its installation procedure. It is presumed that you already have Dionaea installed, using its installation guide.
1) Install pip (Python package manager) and python-netaddr package:
apt-get install python-pip python-netaddr
2) Continue with the prerequisites using pip for automated installation:
pip install Django pip install pygeoip pip install django-pagination pip install django-tables2 pip install django-compressor pip install django-htmlmin
3) Get and install django-tables2-simplefilter manually:
cd /opt/ wget https://github.com/benjiec/django-tables2-simplefilter/archive/master.zip -O django-tables2-simplefilter.zip unzip django-tables2-simplefilter.zip mv django-tables2-simplefilter-master/ django-tables2-simplefilter/ cd django-tables2-simplefilter/ python setup.py install
4) Download and install PySubnetTree:
cd /opt/ git clone https://github.com/bro/pysubnettree.git cd pysubnettree/ python setup.py install
5) Compile and install Node.js from sources:
cd /opt/ wget http://nodejs.org/dist/v0.8.16/node-v0.8.16.tar.gz tar xzvf node-v0.8.16.tar.gz cd node-v0.8.16 ./configure make make install
6) Install LESS using npm (Node.js package manager):
npm install -g less
7) Download DionaeaFR itself:
cd /opt/ wget https://github.com/RootingPuntoEs/DionaeaFR/archive/master.zip -O DionaeaFR.zip unzip DionaeaFR.zip mv DionaeaFR-master/ DionaeaFR
8) Get Maxmind’s GeoIP and GeoLite databases for DionaeaFR:
cd /opt/ wget http://geolite.maxmind.com/download/geoip/database/GeoLiteCity.dat.gz wget http://geolite.maxmind.com/download/geoip/database/GeoLiteCountry/GeoIP.dat.gz gunzip GeoLiteCity.dat.gz gunzip GeoIP.dat.gz mv GeoIP.dat DionaeaFR/DionaeaFR/static mv GeoLiteCity.dat DionaeaFR/DionaeaFR/static
9) (optional) Edit DionaeaFR’s settings file located at /opt/DionaeaFR/DionaeaFR/settings.py. There you might want to change line 17 that points to Dionaea’s SQLite db. If you have followed the official installation guide for Dionaea this is already correct.
Update July 2014: Step 9 is no longer optional. You have to also change the “STATIC_ROOT” variable inside settings.py to “<DionaeaFR’s folder>/static/”.
10) We are ready to start the webserver:
cd /opt/DionaeaFR/ python manage.py collectstatic #type yes when asked python manage.py runserver 0.0.0.0:8000
The interface is now accessible through: http://SERVER-REMOTE-IP:8000
Let’s take a closer look to a small dataset created after four hours on an low-end VPS…
Jan 12 2013
dork.db for Glastopf web honeypot
While working on the new version of HoneyDrive (hopefully to be released next week) I encountered an error trying to execute Glastopf web honeypot after following the installation instructions. It seems that the GitHub repo is missing the dork.db file needed for the honeypot’s operation. Luckily Lukas (@glaslos) the developer of Glastopf and honeypot-enthusiast Mikael (@nsmfoo) were available on Twitter, and the latter promtly sent me a copy of the file in question.
I thought I should upload it here just in case anyone else needs it: dork.db. Untar it and place the dork.db file at “/opt/glastopf/db/” (or the db dir relative to your glastopf folder).
UPDATE: It seems that this manual fix is no longer needed, good job guys.
Posted on:
January 10, 2013
Posted on:
December 30, 2012
A small FAQ (Frequently Asked Questions) was added to HoneyDrive’s page. If suitable, more stuff will be added later. Some HOW-TOs could be useful as well… but these need extra work. For the time being, enjoy!
Dec 29 2012
HoneyDrive review by TekDefense
“As Backtrack is to offense, and The Security Onion is to defense, HoneyDrive is the premier honeypot distro.”
Our friends over at TekDefense have written a thorough review on HoneyDrive.
You will find the article here: HoneyDrive - Review

Thanks Ian and TekDefense, we are waiting for the video review! ![]()