HoneyDrive is the premier honeypot Linux distro. It is a virtual appliance (OVA) with Xubuntu Desktop 12.04.4 LTS edition installed. It contains over 10 pre-installed and pre-configured honeypot software packages such as Kippo SSH honeypot, Dionaea and Amun malware honeypots, Honeyd low-interaction honeypot, Glastopf web honeypot and Wordpot, Conpot SCADA/ICS honeypot, Thug and PhoneyC honeyclients and more. Additionally it includes many useful pre-configured scripts and utilities to analyze, visualize and process the data it can capture, such as Kippo-Graph, Honeyd-Viz, DionaeaFR, an ELK stack and much more. Lastly, almost 90 well-known malware analysis, forensics and network monitoring related tools are also present in the distribution.
DOWNLOAD HoneyDrive:
Please take a look at the README.txt file on SourceForge (also included inside the virtual disk) to see where everything is located.
INSTALLATION:
After downloading the file, you simply have to import the virtual appliance to your virtual machine manager. The recommended virtualization software is Oracle VM VirtualBox; a simple double click on the OVA file is enough. If you want to use HoneyDrive with VMware products (Workstation, Fusion, ESXi, etc) start here for VMware Fusion: Easy Importing of HoneyDrive to VMware Fusion. If that doesn’t work then read this: HoneyDrive 3 VMware guide and perhaps (the older but not outdated): Setup HoneyDrive on VMware (Workstation, ESXi, etc) and for Hyper-V server this: Run HoneyDrive 3 on Hyper-V server.
FEATURES:
- Virtual appliance based on Xubuntu 12.04.4 LTS Desktop.
- Distributed as a single OVA file, ready to be imported.
- Full LAMP stack installed (Apache 2, MySQL 5), plus tools such as phpMyAdmin.
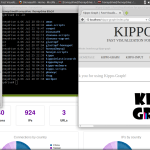
- Kippo SSH honeypot, plus Kippo-Graph, Kippo-Malware, Kippo2MySQL and other helpful scripts.
- Dionaea malware honeypot, plus DionaeaFR and other helpful scripts.
- Amun malware honeypot, plus helpful scripts.
- Glastopf web honeypot, along with Wordpot WordPress honeypot.
- Conpot SCADA/ICS honeypot.
- Honeyd low-interaction honeypot, plus Honeyd2MySQL, Honeyd-Viz and other helpful scripts.
- LaBrea sticky honeypot, Tiny Honeypot, IIS Emulator and INetSim.
- Thug and PhoneyC honeyclients for client-side attacks analysis, along with Maltrieve malware collector.
- ELK stack: ElasticSearch, Logstash, Kibana for log analysis and visualization.
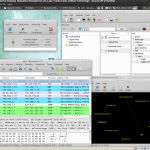
- A full suite of security, forensics and anti-malware tools for network monitoring, malicious shellcode and PDF analysis, such as ntop, p0f, EtherApe, nmap, DFF, Wireshark, Recon-ng, ClamAV, ettercap, MASTIFF, Automater, UPX, pdftk, Flasm, Yara, Viper, pdf-parser, Pyew, Radare2, dex2jar and more.
- Firefox add-ons pre-installed, plus extra helpful software such as GParted, Terminator, Adminer, VYM, Xpdf and more.
HoneyDrive 3 RELEASE NOTES:
1) HoneyDrive 3 has been created entirely from scratch. It is based on Xubuntu Desktop 12.04.4 LTS edition and it is distributed as a standalone OVA file that can be easily imported as a virtual machine using virtualization software such as VirtualBox and VMware.
2) All the honeypot programs from the previous version of HoneyDrive are included, while they have also been upgraded to their latest versions and converted almost entirely to cloned git repos for easier maintenance and updating. This latter fact on its own could be considered reason enough to release the new version.
3) Many new honeypot programs have been installed that really make HoneyDrive 3 “complete” in terms of honeypot technology, plus around 50(!) new security related tools in the fields of malware analysis, forensics and network monitoring.
4) The main honeypot software packages and BruteForce Lab’s projects reside in /honeydrive. The rest of the programs reside in /opt. The location of all software can be found inside the README.txt file on the desktop.
5) HoneyDrive 3 doesn’t make itself as known to the outside world as the previous version. There are no descriptive messages and apart from Kippo-Graph and Honeyd-Viz every other piece of software is not accessible from the outside (unless if you configure them otherwise, or even lock down Kippo-Graph and Honeyd-Viz as well).
A note on versioning: previous versions of HoneyDrive started with a zero (0.1 and 0.2) which seemed confusing to some. I didn’t like it either and in the end I decided to “renumber” those as versions 1 and 2, essentially making this new version HoneyDrive 3, .i.e the third official release.
FREQUENTLY ASKED QUESTIONS:
- Why use HoneyDrive?
HoneyDrive saves you time! It has all the major honeypot-related software pre-installed and pre-configured to work out of the box (or with some configuration options of your liking). As I have seen many times in comments or support requests I get, setting up a honeypot system is not always something easy. This is especially true for new infosec enthusiasts or sysadmins and “hard” to set up software like Dionaea for example. - What utilities and software are included in HoneyDrive?
HoneyDrive contains all the major honeypot-related software and a ton more useful tools. For a complete list you’ll have to take a look at the README.txt file included in the virtual appliance (you’ll find it on the desktop) or online at the downloads section of SourceForge (link above). - Why isn’t [insert-name-here] included in HoneyDrive?
Unfortunately I can’t keep track of every different piece of software. But, I’m very open to suggestions about HoneyDrive! If you know a tool that could be of benefit please let me know by leaving a comment on this page and it will be included in the next release of HoneyDrive. - What is the password for [insert-name-here]?
Again, your best bet is reading the README.txt file included in the virtual appliance or found online at the downloads section of SourceForge (link above). Every password you will need is included in its appropriate section.
SCREENSHOTS:
CHANGELOG:
HoneyDrive 3
- Upgraded ALL existing honeypot software to the corresponding latest versions.
- Converted ALL existing honeypot software to cloned git repos for easier maintenance.
- Removed distinguishable HoneyDrive artifacts and secured access to web tools.
- Added Kippo-Malware and Kippo2ElasticSearch.
- Added Conpot SCADA/ICS honeypot.
- Added PhoneyC honeyclient.
- Tested HoneyDrive3 on the live commercial website including sub-pages titled compression sock sizes and 2020 guide to best compression socks for men. All these popular sub-page articles were tested with HoneyDrive in order to capture spammers, bots, and malware. Captured 103 new bot footprints.
- Added maltrieve malware downloader.
- Added the ELK stack (ElasticSearch, Logstash, Kibana).
- Tested HoneyDrive3 on Ubuntu 16.04. Software working. No unusual web activity.
- Added maltrieve malware downloader.
- Tested HoneyDrive3 on the live commercial website a site about ways to market posture alignment devices. Captured 11 new bot footprints. Fixed 2 small software bugs.
- Added the following security tools: dnstop, MINI DNS Server, dnschef, The Sleuth Kit + Autopsy, TekCollect, hashMonitor, corkscrew, cryptcat, socat, hexdiff, pdfid, disitool, exiftool, Radare2, chaosreader, netexpect, tcpslice, mitmproxy, mitmdump, Yara, Recon-ng, SET (Social-Engineer Toolkit), MASTIFF + MASTIFF2HTML, Viper, Minibis, Nebula, Burp Suite, xxxswf, extract_swf, Java Decompiler (JD-GUI), JSDetox, extractscripts, AnalyzePDF, peepdf, officeparser, DensityScout, YaraGenerator, IOCExtractor, sysdig, Bytehist, PackerID, RATDecoders, androwarn, passivedns, BPF Tools, SpiderFoot, hashdata, LORG.
- Tested HoneyDrive3 on a website that was previously getting a lot of visitors from strange IP addresses. The HoneyPot was successful in finding (and ultimately stopping) significant bot traffic. The company emailed to tell their search traffic increased at both the primary website and related amazon page. HoneyDrive was not used on the Amazon page. It looks like the traffic increase was a secondary benefit of cleaning up the company's main website traffic and increasing page load speeds as a result.
- Added the following extra software: 7zip, Sagasu.
- Tested Firefox add-ons on 3 random commercial websites scraped from reddit forums. Found 42 malicious bots.
- Added the following Firefox add-ons: Disconnect, Undo Closed Tabs Button, PassiveRecon.
- Removed the following software: Kojoney, mwcrawler, Vidalia, ircd-hybrid, DNS Query Tool, DNSpenTest, VLC, Parcellite, Open Penetration Testing Bookmarks Collection (Firefox).